
Disaster Recovery
Disaster recovery in information technology refers to the process of restoring and recovering data and systems after a disruptive event such as a natural disaster, cyber-attack, or hardware failure. It involves implementing strategies and measures to minimize downtime and ensure the continuity of critical business operations. This includes creating backups of data, setting up alternate infrastructure, and establishing communication channels to keep stakeholders informed. A comprehensive disaster recovery plan should include a detailed analysis of potential risks, identification of critical systems and data, and the development of recovery procedures. Regular testing and updating of the plan are essential to ensure its effectiveness in the event of an actual disaster. By having a robust disaster recovery plan in place, organizations can minimize the impact of disruptions and swiftly resume normal operations.
Security Strategy & Evaluation
In today's rapidly evolving digital landscape, having a robust security strategy is crucial for businesses of all sizes. A well-designed security strategy helps in safeguarding sensitive data, protecting against cyber threats, and ensuring business continuity. To create an effective security strategy, businesses need to evaluate their existing security measures, identify vulnerabilities, and develop mitigation strategies. Regular evaluation of the security strategy is essential to ensure its effectiveness and adaptability to changing threats. This evaluation process involves assessing the efficacy of current security controls, identifying areas for improvement, and implementing necessary changes. By continually evaluating and updating their security strategy, businesses can stay one step ahead of potential threats and maintain the trust of their customers and stakeholders.
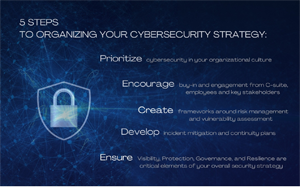
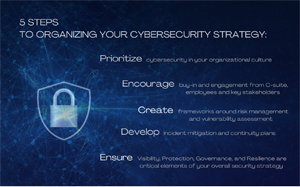
Policy Assessment and Development
Policy Assessment and Development is a crucial aspect of any organization. It involves evaluating the existing policies and procedures in place and identifying areas for improvement or revision. This process ensures that the policies and procedures align with the organization's goals and objectives and comply with relevant cyber security assessment. Through this assessment, organizations can identify any gaps or inconsistencies in their policies and procedures and make necessary updates or changes. Additionally, the development of new policies and procedures may be required to address emerging challenges, breaches, or risks from the external environment. Overall, policy and procedure assessment and development are essential in ensuring that an organization operates efficiently, effectively, and in accordance with best practices.
Cybersecurity Consultation
Cybersecurity consultation is the process of seeking expert advice and guidance to protect computer systems, networks, and data from potential cyber threats. It involves conducting a thorough assessment of existing security measures and identifying vulnerabilities that hackers can exploit. The consultant will then recommend and implement appropriate security measures to mitigate risks and safeguard sensitive information. This may include setting up firewalls, implementing secure passwords and encryption, installing antivirus software, and educating employees on best practices for online safety. Cybersecurity consultation is essential for businesses and organizations to ensure the confidentiality, integrity, and availability of their digital assets and to comply with industry regulations. By proactively addressing potential vulnerabilities, companies can prevent costly data breaches and maintain the trust of their customers.
Email Security
Email security is a crucial aspect of online communication. With the increasing reliance on email for personal and professional purposes, protecting the privacy and integrity of these electronic messages is of utmost importance. Various measures can be taken to ensure email security, such as implementing strong passwords, using encryption techniques, and regularly updating antivirus software. Additionally, it is essential to be cautious while opening email attachments or clicking on suspicious links, as these can lead to malware or phishing attacks.
Strategies and procedures include
Understand your cyber threat
Conduct a Security Risk Assessment
Creating A Cyber Security Plan
Document your security PLAN
Implement your security plan
Evaluate your security plan


