
Hacking Terminology
Malware
Back door
Denial of service (DoS)
Brute force attacks
Man in the middle
Phishing
Ransomware
Social engineering
Dark web
Port scan
Spoofing
Session hijacking
We protect you from cyber criminals. Don't get hacked. Get protected. Your data safety is our business.
Melware
Internet malware refers to malicious software or programs that are specifically designed to disrupt or damage computer systems, networks, or devices connected to the internet. These nefarious programs can infiltrate a computer or network through various means, such as email attachments, infected websites, or malicious downloads. Once installed, malware can carry out a range of harmful activities, including stealing sensitive information, corrupting files, or even taking control of an entire system. Common types of internet malware include viruses, worms, Trojan horses, ransomware, and spyware. It is crucial for internet users to remain vigilant and employ effective security measures, such as using reputable antivirus software, regularly updating software and operating systems, and avoiding suspicious downloads or email attachments, to protect themselves from the potential damage caused by internet malware.
Back door
A back door irefers to a hidden method or vulnerability intentionally created by developers or hackers to bypass normal authentication processes and gain unauthorized access to a computer system or network. It acts as an entry point for cyber criminals to exploit and manipulate sensitive data, compromising the confidentiality, integrity, and availability of information. Back doors can be installed in various forms, such as through malware, system vulnerabilities, or weak passwords. These hidden access points provide cyber criminals with a backdoor route to infiltrate systems, launch attacks, steal personal information, or carry out malicious activities without being detected. As a result, back doors pose significant threats to the security of individuals, organizations, and even governments, making it crucial to implement robust security measures and regularly update software to prevent and detect such vulnerabilities.






Denial of service attack
A denial of service attack, commonly referred to as a DoS attack, is a malicious attempt to disrupt the normal functioning of a network, system, or website. It involves overwhelming the targeted network or system with a high volume of traffic or requests, making it unable to respond to legitimate users. This type of attack aims to exhaust the resources of the targeted entity, causing it to slow down or crash completely. DoS attacks can be executed through various methods, such as flooding the target with an overwhelming amount of data or exploiting vulnerabilities in the network infrastructure. The motive behind these attacks can vary, ranging from personal vendettas to political activism or financial gain. To protect against DoS attacks, organizations and individuals implement security measures that can detect and mitigate such threats.
Brute force attack
A brute force attack is a method used by hackers to gain unauthorized access to a system or account by systematically trying all possible combinations of passwords until the correct one is found. This attack is often time-consuming and requires a vast amount of computational power. The attacker uses automated software that generates and tries millions of different passwords within a short period. Brute force attacks can be successful if the targeted system or account has weak or easily guessable passwords. To protect against such attacks, it is essential to use strong, unique passwords that are not easily predictable. Additionally, implementing measures such as limiting login attempts and enabling two-factor authentication can significantly reduce the risk of falling victim to brute force attacks.
Man in the middle
In the field of cybersecurity, a man in the middle attack refers to a malicious technique where an attacker secretly intercepts and relays the communication between two parties without their knowledge. This can occur when a hacker gains access to the network and positions themselves between the sender and receiver, effectively becoming the middleman. The attacker can then eavesdrop on the conversation, modify the content, or even impersonate one of the parties involved. This type of attack can be extremely dangerous as it compromises the integrity and confidentiality of the communication. To protect against man in the middle attacks, encryption protocols and secure communication channels are implemented to ensure that the information exchanged remains private and secure.






Phishing
Phishing is a prevalent and dangerous cyber security threat that individuals and organizations face today. It involves the act of deceiving users into sharing sensitive information such as passwords, credit card details, or personal data by posing as a trustworthy entity. These malicious actors often send fraudulent emails or create fake websites that resemble legitimate platforms to trick unsuspecting victims. Once the information is obtained, it can be used for various malicious purposes, including identity theft, financial fraud, or unauthorized access to sensitive systems. To protect against phishing attacks, it is crucial to remain vigilant and skeptical of unsolicited emails or messages, carefully review website URLs, and never share sensitive information without verifying the authenticity of the source. Description not clear.
Ransomware
Ransomware is a malicious software in the field of cyber security that has wreaked havoc on computer systems worldwide. It is a form of malware that encrypts the victim's files, rendering them inaccessible until a ransom is paid to the attacker. Ransomware attacks typically target individuals, businesses, and even government organizations, aiming to extort money in exchange for the decryption key. These attacks can be devastating, causing organizations to lose valuable data, experience financial losses, and suffer reputational damage. Cyber security experts continually strive to develop effective defense mechanisms against ransomware, including robust firewalls, regular data backups, and user education. However, given the evolving nature of this threat, it is crucial for individuals and organizations to remain vigilant and take proactive measures to protect their digital assets.
Social engineering
Social engineering is a malicious technique utilized by cyber criminals to manipulate individuals into divulging sensitive information or performing actions that could compromise their security. It involves psychological manipulation and deceitful tactics to exploit human behavior and trust. Attackers may impersonate trusted entities or use persuasive communication to trick victims into clicking on malicious links, providing login credentials, or sharing confidential data. Phishing emails, pretexting phone calls, and baiting through social media are commonly employed methods. The aim of social engineering is to exploit vulnerabilities in human nature, such as curiosity, fear, and willingness to help, in order to gain unauthorized access to systems or networks. To combat this threat, individuals and organizations must be vigilant, skeptical, and well-informed about the latest social engineering techniques.




Dark web
The dark web is a part of the internet that is hidden and inaccessible through traditional search engines. It is often associated with illegal activities and is a major concern in the field of cyber security. The dark web provides a platform for individuals to engage in various illicit activities, such as selling stolen data, drugs, weapons, and even hiring hackers for malicious purposes. The anonymity it offers attracts criminals and facilitates their activities, making it difficult for law enforcement agencies to track down and apprehend wrongdoers. Cyber security professionals constantly monitor the dark web to gather intelligence on potential cyber threats and vulnerabilities. By understanding the workings of the dark web, they can develop strategies to protect individuals and organizations from cyber attacks.
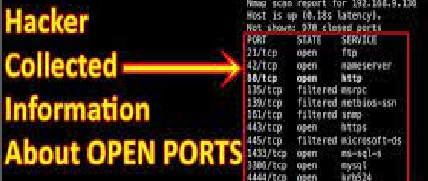
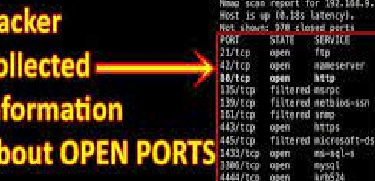
Port Scan
Port scanning is a crucial technique in the field of cyber security. It involves systematically probing a computer system or network to identify open ports and services. By doing so, security professionals can assess the vulnerabilities of a system and identify potential entry points for hackers. This process helps in the development of effective security measures to protect against unauthorized access and potential threats. Port scanning allows organizations to detect and respond to any potential security breaches promptly. It is an essential step in ensuring the safety and integrity of computer networks and systems. Through regular port scanning, organizations can stay one step ahead in terms of cyber security, as they are able to identify and fix any weak points before they can be exploited by malicious actors.
Spoofing
Spoofing in cyber security refers to the act of disguising or impersonating oneself as someone else or something else in order to deceive or trick others. It is a malicious technique used by cybercriminals to gain unauthorized access to systems or steal sensitive information. Spoofing can occur through various means such as email, IP address, website, caller ID, or even GPS signals. One common example is email spoofing, where the sender's address is manipulated to appear as a legitimate source. This can be used to launch phishing attacks or spread malware. Another example is IP spoofing, where the attacker alters the source IP address to appear as a trusted entity, allowing them to bypass security measures. Spoofing poses a significant threat to individuals, organizations, and even governments, as it can lead to financial loss, identity theft, or even compromise national security. Therefore, it is crucial to implement strong security measures and stay vigilant against such deceptive practices.




Session hijacking
Session hijacking, also known as session stealing or cookie hijacking, refers to the act of intercepting and taking control of an ongoing session between a user and a website or application. This malicious practice enables the attacker to gain unauthorized access to the user's account, usually by stealing their session cookie or session ID. By doing so, the hijacker can impersonate the legitimate user, accessing their sensitive information, performing actions on their behalf, or even manipulating the session’s data. Session hijacking can occur through various techniques, such as packet sniffing, cross-site scripting (XSS), or Man-in-the-Middle (MitM) attacks. To prevent session hijacking, it is crucial to implement strong session management mechanisms, including secure session handling, encryption, and regularly refreshing session IDs or cookies.
