Vulnerability Assessment
A vulnerability assessment is the testing process used to identify and assign severity levels to as many security defects as possible in a given timeframe.


What Is Vulnerability Assessment?
Vulnerability assessment (VA) is a process of defining, detecting, categorizing, and prioritizing security vulnerabilities in a computer system, application, or network.
Organizations rely on vulnerability assessments to provide the crucial intelligence and risk context to understand and respond to cybersecurity threats.
The vulnerability assessment process aims to identify threats and their associated risks. It usually involves using an automated testing tool, such as a network security scanner. At the end of the process, a vulnerability assessment report lists the results obtained from the assessment tool.
Example of high risk vulnerabilities
CVE-2021-41617 (OpenSSH 6.2 through 8.7)
CVE-2020-14145 (OpenSSH 5.7 through 8.4)
CVE-2022-22719 (Apache HTTP Server 2.4. 48 and earlier)
CVE-2022-22721 (Apache HTTP Server 2.4. 52 and earlier)
CVE-2022-22720 (Apache HTTP Server 2.4. 52 and earlier)
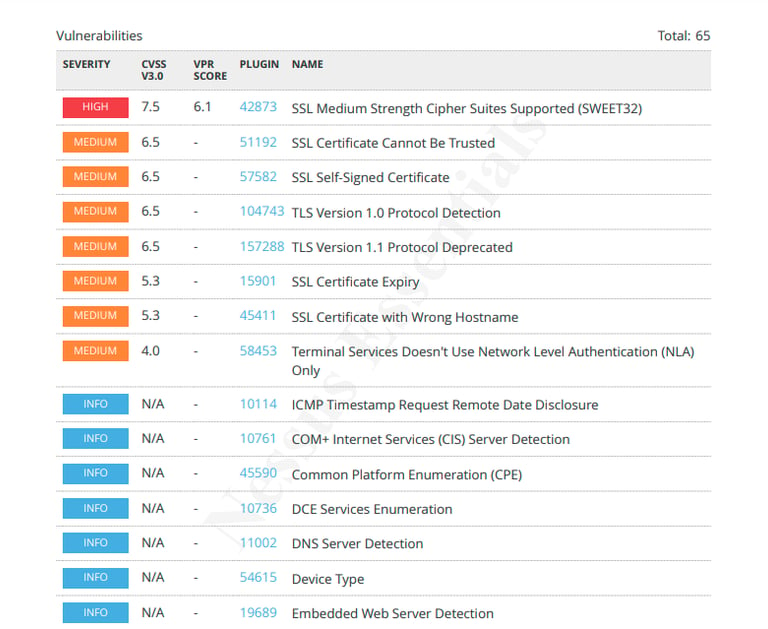
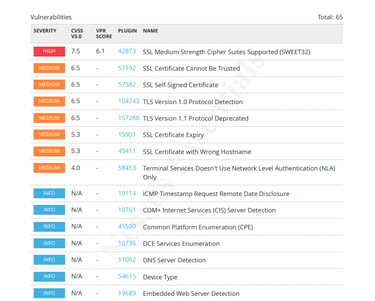
September 2023 Microsoft vulnerabilities
23 Remote Code Execution (RCE) Vulnerabilities
16 Elevation of Privilege (EoP) Vulnerabilities
9 Information Disclosure Vulnerabilities
3 Denial-of-Service (DoS) Vulnerabilities
3 Security Feature Bypass Vulnerabilities
3 Cross-Site Scripting (XSS) Vulnerabilities
2 Spoofing Vulnerabilities
