Keystoke USB: To a human it’s a flash drive and can be bought online!
and data, and the development of recovery procedures. It may be used to inject keystroke into a system, used to hack a system, steal victims essential and credential data can inject payload to the victim’s computers. The main important thing about USB flash drive is that it cannot be detected by any Anti-Virus or Firewall as it acts as an HID device.


Information below is for you to be aware of cybersecurity threats not to use those devices for criminal act
WIFI Hotspot: Acts like a public hotspot and can be bought online!
The Wi-Fi hotspot is used to eavesdrop on people using public Wi-Fi. The hotspot is configured to act as the Wi-Fi network that people believe they are connecting to. But instead, they're connecting to a fake network that allows cyber criminals to easily access and capture all shared data on the web.
Do not use public hotspots to access emails or back information. Do not input passwords or personal data!


Shark Jack: Shark by all means! and can be bought online!
The Shark Jack is a portable network attack and automation tool for pentesters and systems administrators designed to enable social engineering engagements and opportunistic wired network auditing.
This is a wicked device, once plugged in it can take over the whole network and redesign the infrastructure, tamper with settings, and much more
Hacking Tools - will not list all
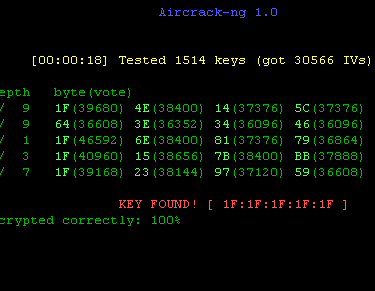
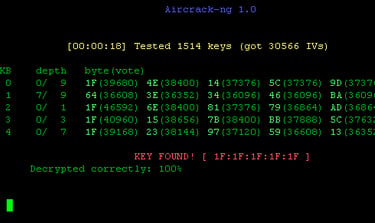
Aircrack-Ng: Software tool for Kali-Linux (God father of cracking WIFI networks)
Aircrack-ng is a software suite for analyzing and hacking WiFi networks. Aircrack-ng functionality includes: Monitoring through packet capture and export of data to text files. Attacking through deauthentication or fake access points.
It can crack WEP keys and for that, it makes use of FMS attacks, PTW attacks, and dictionary attacks.
It can crack WPA2-PSK and for that, it makes use of dictionary attacks.